defmodule App.Restrict.AllowIframe do
@moduledoc """
Allows affected ressources to be open in iframe.
alias Plug.Conn
def init(opts \\ %{}), do: Enum.into(opts, %{})
def call(conn, _opts) do
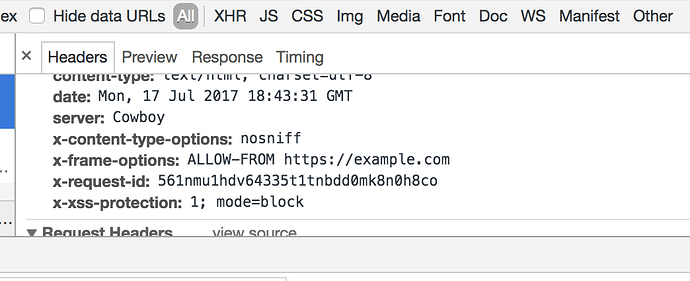
Conn.put_resp_header(conn,"x-frame-options","ALLOW-FROM https://example.com")
ok, now I remember  This worked fine but I wanted more then one exception, tried comma / space separated and then switched to removing the header.
This worked fine but I wanted more then one exception, tried comma / space separated and then switched to removing the header.
I googled it now and it seems indeed to be a limitation https://stackoverflow.com/questions/10205192/x-frame-options-allow-from-multiple-domains
So it’s x-frame-options for one domain or content-security-policy for more.
I’m working on allowing iframe embeds from another site to my phoenix server.
Here’s the trouble I’m running into:
doing Conn.put_resp_header(conn, "content-security-policy", "frame-src" 'self' https://mydomain")
results in the frame not displaying due to an error of ‘x-frame-options’ being set to “SAMEORIGIN” in chrome.
doing Conn.put_resp_header(conn, "x-frame-options", "ALLOW-FROM https://mydomain")
as suggested above allows the iframe to work. However, I still get an error, even though the frame displays.
Problem: This doesn’t seem to be a whitelist, but I’m not certain.
The iframe is properly displaying on my whitelisted domain, on a completely different webservice than my Phoenix server. However, I can use a different computer, not on the white list, to display an iframe containing the site when hosted locally with a simple index.html and <iframe> tag.
The error it displays when running the index.html on my local, non-whitelisted computer is:
Invalid 'X-Frame-Options' header encountered when loading 'http://myPhoenixServer 'ALLOW-FROM https://MyOtherHost' is not a recognized directive. The header will be ignored.
But, it still pulls the webpage from the phoenix host and displays it in the iframe, CSS/JS/HTML and all.
Sorry I am replying to this one year later, just throwing this out there so if someone else finds this thread is does not run into the same thing.
According to the spec the option "allow-from https://example.com/" is not supported in Chrome or Safari, that is probably why you ran into this issue.
it seems that frame-ancestors overrides x-frame-options so all you need to do is something like:
defp framething(conn, _) do
put_resp_header(conn,"x-frame-ancestors","'self' https://<CHROME ID>.chromiumapp.org")
 This worked fine but I wanted more then one exception, tried comma / space separated and then switched to removing the header.
This worked fine but I wanted more then one exception, tried comma / space separated and then switched to removing the header.